The need for enhanced cooperation of the Western powers in the field of Defence was underlined by Mr. Nikolaos Papatsas, Senior Partner of…

Mr. Ioannis Ioannidis, the man who leads Deloitte Cyprus’ Cyber Risk Services, participated in the “Armed and Security Forces Synergies” session during the BATTLEFIELD ReDEFiNED 2023 International Conference held in Cyprus.
In his presentation entitled “Cyberwarfare – The unseen battlefield”, Mr. Ioannidis referred to the most modern form of warfare and its effects, cyberwarfare.

First, Mr. Ioannidis pointed out the main types of cyberwarfare with reference to “phishing” – phishing attacks aimed at stealing or damaging sensitive data by tricking people into revealing personal information such as passwords and credit card numbers – and ransomware – a type of malware or malicious software that threatens the victim by destroying or blocking access to crucial data or systems until a ransom is paid. In fact, these are methods that have evolved into the most rampant forms of cybercrime.
Furthermore, Mr. Ioannidis referred to the term “hacktivism”, which is widespread due to the recent developments in Ukraine. It is a method of activism on the Internet through the use of malicious software, which aims to incite political disobedience and protest (Protestware) for the promotion of a political agenda or social change.
The speaker then decoded the objectives of such malicious attacks as follows:
- Disruption of critical services
- Achieving political and psychological results through propaganda and fear tactics
- Derailment of military transport and humanitarian aid
- Disruption of public access to services and media
- Stealing information and data to extract information or economic value
Also read: Medusa ransomware | Claims responsibility for cyberattack on the Open University of Cyprus
The presentation continued with Mr. Ioannidis placing emphasis on a particularly critical aspect of cyber attacks: supply chain attacks.
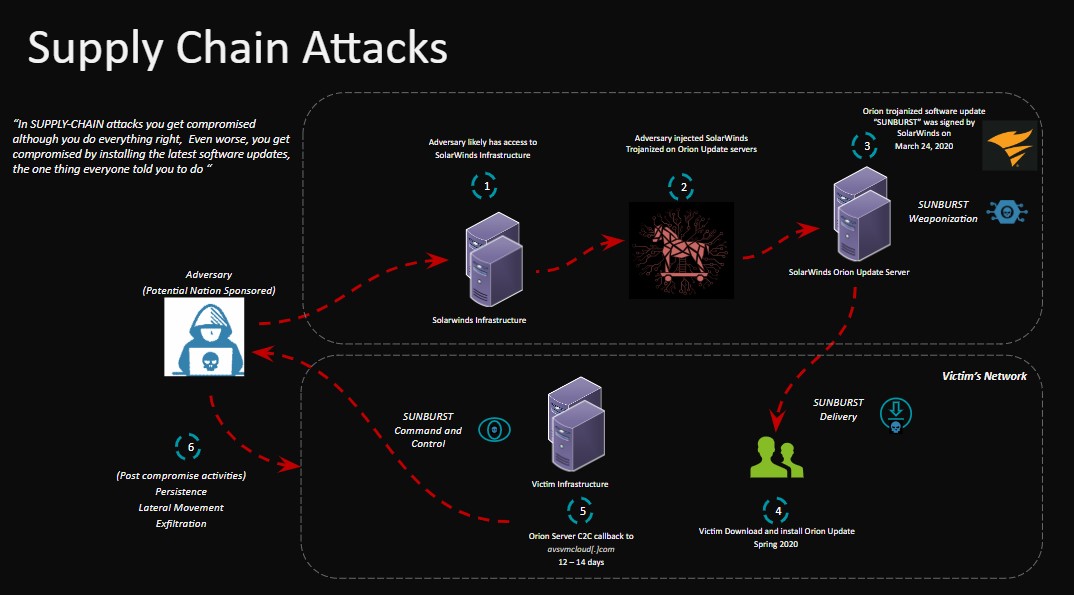
Supply chain attacks are an emerging threat, targeting the software of outside developers and suppliers. In this way, attackers seek to gain access to source codes, create processes or update mechanisms by infecting legitimate applications to distribute malware.
For example, by delivering viruses or other malware through a provider, an infected USB drive can enter a company and, during its use, steal passwords.
Also read: Cyprus | Government websites down due to water leak – The value of Data Centers
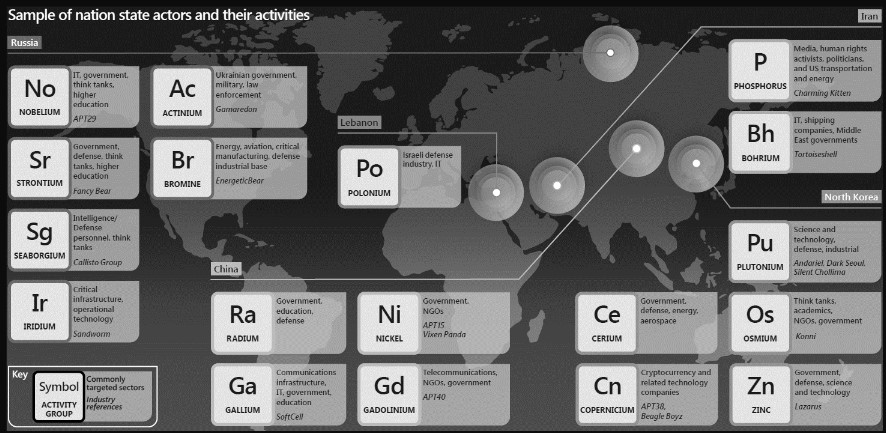
In addition, Mr. Ioannidis made special mention of cyber attack activities at the state level with the obvious purpose of promoting national interests. These mainly concern:
- Intellectual property theft
- Espionage
- Surveillance
- Sponsorship of operations
- Credential theft
- Destructive attacks
According to Mr. Ioannidis, targets of cyber attacks are sectors such as Information Systems, Non-Governmental Organizations, Education, Transport, Governments, and Health.
Finally, Mr. Ioannidis attempted to get across to the delegates the scope of the severity of the impact of such malicious activities in terms of public safety by referring to the Blackout in Kyiv in 2016, where 3 million people were left without power due to a modular, automated and widespread cyber attack.
Also read: Ukraine | Massive cyberattack on government websites
READ MORE
Delphi Economic Forum IX | Christian Chatziminas on re-industrialization and high technology in entrepreneurship
Mr. Christian Chatziminas, Founder & CEO of THEON GROUP and President of the Hellenic Entrepreneurs Association, participated in…
Heraklion | Aerial target washes up on beach – Taken for drone from Iran
Yesterday Sunday, intense confusion was caused on a beach in Heraklion, Crete, when an aerial target used in shooting ranges to test…
A reluctant alliance? A different approach to French – Serbian defence relations
It has only been a few months since Croatia started receiving the first of the Rafale fighter jets it ordered from France.
Elliniko | 314 bombs buried at former airport
Over 300 bombs from the Second World War have been found at the old airport of Athens in Elliniko. The news about the said…
Agamemnon | The new Astute-class HMS nuclear submarine of the Royal Navy
The British Royal Navy has named the newly-built Astute-class nuclear-powered submarine HMS Agamemnon. Doing so, the…
NSPA | Awards first C-sUAS multinational contract in NATO’s history
The NATO Support and Procurement Agency (NSPA) has approved the first Counter-small UAS (C-sUAS) procurement framework agreement…
USA | Signs bill on military aid to Ukraine
US President Joe Biden has signed a bill providing Ukraine with billions of dollars in new aid for its war with Russia, marking a rare…
Armenian Genocide Remembrance Day
On this day, 109 years ago, the genocide of the Armenian people by the Ottoman Empire began, with April 24 being the day of…






















